Cyber Threat Intelligence Weekly Report (Sep 29 – Oct 5, 2025)
3 min read
Cyber Threat Intelligence Weekly Report
Coverage window: Sep 29 – Oct 5, 2025.
Scope: Ransomware posts (global) + 126 traditional breaches + 103 new stealer packages.
Headline Metrics
• Ransomware: dozens of victims posted across NA, EU, LATAM, MENA, and APAC
• Traditional breaches: 126 newly observed (non-ransomware)
• Stealer ecosystem: 103 new infostealer packages fueling credential abuse
Most Impactful / Sensitive Cases This Cycle
• Shamir Medical Center (IL) — Qilin: claimed ~8 TB of sensitive hospital data; high patient-safety & privacy risk.
• Comcast (US) — Medusa: alleged ~834 GB affecting a major media/telecom operator; potential customer/infra exposure.
• CCMC (US) — Medusa: ~2.92 TB exfiltration from large community association manager; broad PII/financial footprint.
• Organon (US) — Medusa: ~478 GB from global pharma; IP and PHI concerns.
• Insightin Health (US) — Medusa: ~378 GB from healthcare analytics SaaS; payer/member data risk.
• Future Generali (IN) — Medusa: ~387 GB from insurance JV; sensitive policyholder data.
• Banco Hipotecario del Uruguay (UY) — Crypto24: ~700+ GB including
• High-sensitivity customer PII and core banking docs.
• ShinyHunters “mega-claims”: mass list of marquee brands (e.g., Cisco, TransUnion, IKEA, Adidas, Kering, Marriott, UPS, FedEx, Toyota, etc.). Treat as claims until validated; potential brand-targeted phishing surge.
• Public sector & utilities: Lakehaven Water District (US) — Qilin, **Saginaw Chippewa Tribe (US) — Qilin, Hillside Public Library (US) — Incransom.
• Industrial/critical suppliers: IONODES (CA) — Qilin (video/IoT), Mitchell Industries (US) — Qilin (energy/refining components), Stockmeier Urethanes (DE) — Incransom (chemicals), Terex Environmental Group (CA) — Incransom (env. consulting).
• Legal & professional services: multiple law firms (e.g., Mitrani Rynor Adamsky & Toland — Qilin), Greenville Legal — DragonForce.
• Education & health: Watsonville Community Hospital (US) — Sinobi, Western Orthopaedics (US) — Pear, Shamir Med Center (IL) — Qilin.
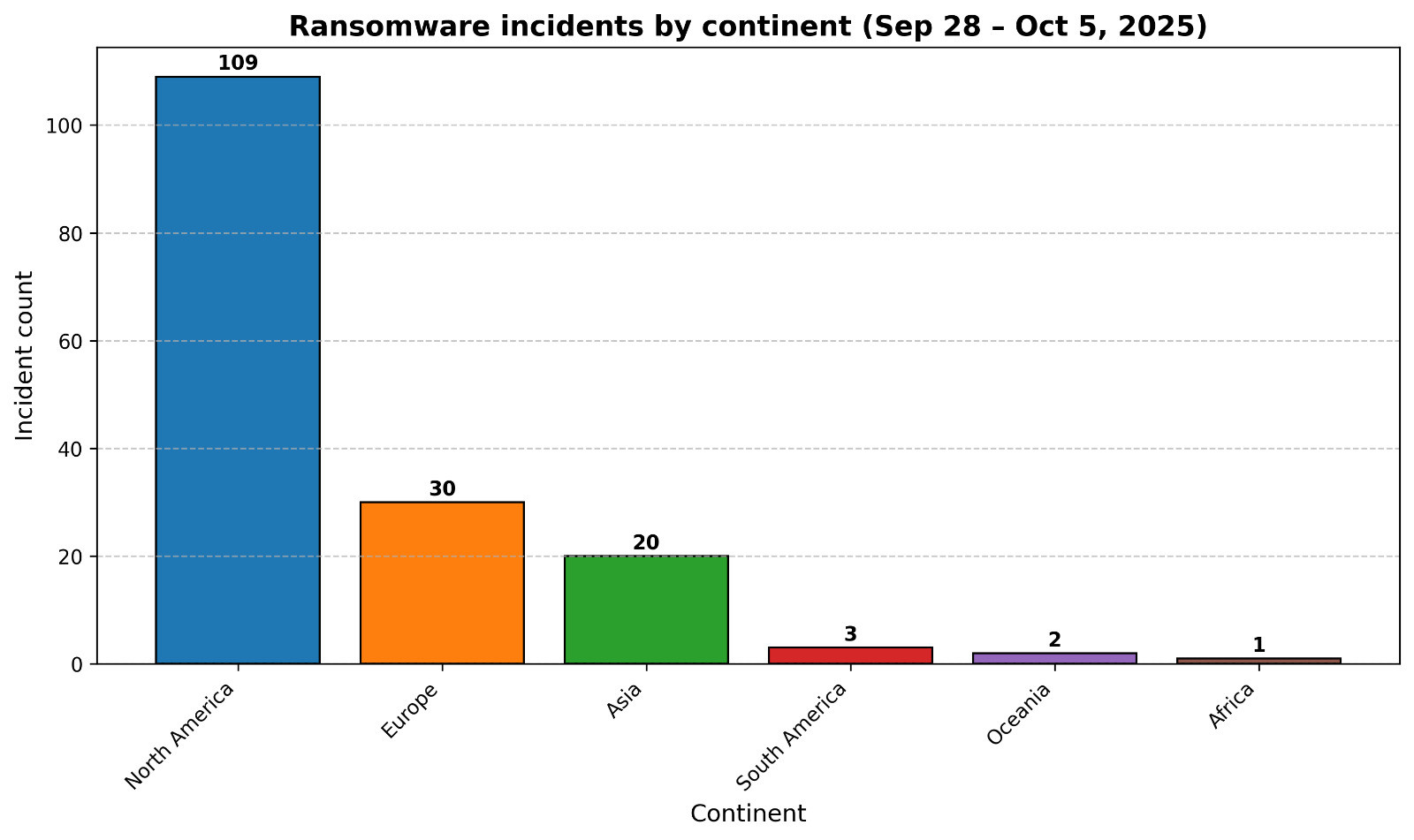
Actor & TTP Notes
• Ransomware crews most active: Medusa, Qilin, Akira, Incransom, Sinobi, Securotrop, DevMan, Beast, Play.
• Extortion-first patterns: multiple posts with ransom demands + exfil sizes; some publish sample directories and countdown threats.
• Supply-chain pressure: hits on manufacturing, chemicals, construction, IoT video, MSP/IT, and logistics amplify downstream risk.
• Data volumes escalating: several hundreds of GB to multi-TB leaks reported, increasing legal/regulatory exposure.
• Infostealers: 103 new packages add credential replay and initial access risk for enterprises and SaaS (O365, VPN, CRM, ERP).
Sector Impact (selected)
• Healthcare & Life Sciences: hospitals, pharma, health SaaS (PHI/PII, compliance triggers).
• Financial: bank (UY), asset managers (US/KR/HK/CA); fraud & insider-risk vectors.
• Government/Public/Utilities: tribes, water districts, libraries; critical service disruption potential.
• Industrial & Energy Supply Chain: chemicals, HVAC/building controls, pulp/paper, precision manufacturing.
• Retail/CPG & Hospitality: logistics operators, hotels, home goods; payment and loyalty data at risk.
• Education: universities and K–12-adjacent orgs.
Likely Near-Term Risks
• Credential replay & MFA fatigue driven by the 103 stealer packages.
• Brand-impersonation waves abusing ShinyHunters “big-logo” claims to lure victims (phishing, malvertising).
• Double/triple extortion escalation (data leak → harassment of customers/partners → DDoS).
Recommended Actions (Priority)
1. Account hardening (7–14 days):
Enforce FIDO2/WebAuthn for admins & VIPs; disable legacy/exchange basic auth; conditional access by geo/device posture. Rotate all shared secrets on any vendor/SaaS tied to listed victims.
2. Stealer exposure sweep (48–72h):
Cross-match corporate emails/domains with *fresh stealer logs; force-reset and revoke refresh tokens; invalidate API keys.
3. Third-party risk controls (this week):
Notify business owners for vendors in health, finance, logistics, chemicals, construction/IoT video; request IOC/IOA attestations and token/key rotation.
4. Data-loss controls:
Tag & monitor *customer/health/financial* data; DLP for exfil channels (cloud drives, personal email, paste).
5. Detection engineering:
Hunt for rclone/megalodon/s3sync, archive staging in temp paths, and common Medusa/Qilin/Akira tooling; watch Tor/MEGA/AnonFiles traffic egress.
6. Comms & legal readiness:
Pre-draft *customer & regulator notices; map breach-notification clocks for HIPAA/GDPR/LGPD/CCPA depending on your footprint.
Discover all attacks and leaks and check if your data has been compromised at:
